BGINFO - A Posh Recreation
Recently I have been building a lot of Windows Servers in different environments - one
I love PowerShell – I have a blog about PowerShell! I not been doing much cause of different projects and things in life drawing me away for a couple of month! So once again sorry about the Gap, but my Daughter Ava is worth it!
I got asked a question today, which lead me right to my PowerShell prompt! “Grumpy Admin, what security and logging can we enable to track PowerShell cmdlet usage over the server estate?”. Excellent Question, and one with 5 mins of Admin work, (bit longer as I decided to get coffee and take screenshots for this blog post”) I got a POC working to demo… unlike some people (glares at his boss) I don’t do willy dilly changes to production systems, without testing in a POC lab or testing/staging area! Change control guys, it’s not a SIN!
So as this is a very easy blog to get me back into the swing of things.
So system wide PowerShell logging is quite useful thing! I have covered transcripts in the past on my blog using the
start-transcript ( http://hazzy.techanarchy.net/posh/powershell/console-trans-tripping/ ).
Let’s take this a step more forward this is quite helpful, when you have a pointed headed boss, who likes to do random stuff while troubleshooting unconnected issues and doesn’t document what he did so you have undocumented system changes… which really really really makes Grumpy Admin … GRUMPY, which turns even the most fun loving admin in to a raging homicidal killer!
Let’s throw some of that Windows Admin magic at the problem! Let’s get some GPO action on the go!
Right, so we going to store the transcripts in a central location, we are using Windows so an SMB share to a folder is perfect!
As this is a small lab, I will just create a directory on my c:\ called security and then inside there a directory call poshlogs!
Next I need to create is an SMB Share. I must point out, using PowerShell we can take advantage of the pipeline – but so I can stretch out my blog word count, we will do it command at a time!
So let’s use the cmdlet, new-smbshare to create our SMB share, remember the golden rule with PowerShell it think, say, do….
new-smbshare -name Logs -Path c:\security\poshlogs -encryptdata $true
We all should be using modern OS’s these days that support the end to end encryption features of SMB protocol (not version 1), this helps to protect against Man in the middle attacks! So I always try to ensure data is encrypted!
Now a good thing to do, if you don’t have any older SMB protocol machine around in your network, is to disable the old SMB 1 protocol. Let have a look and see if this older protocol is enabled on our server. (HINT default it is).
But to be sure, let’s just check our SMB server configuration using the very helpful cmdlet
get-smbserverconfiguration
as you can see from the screenshot, the EnableSMB1protocol is set to true! Eck, lets stick our fingers up to Windows XP clients and disable this!
set-smbserverconfiguration -enablesmb1protocol $false
we can do another get-smbserverconfiguration to confirm, as we all know, Grumpy Admin likes to confirm things are done. As you can see it’s done, don’t get confused with the EncryptDate $false.

If we set this to true, then all share will be encrypted… I like to think that this is a good thing, but at the moment, I just want my logs share done as that is what this Proof of Concept is!
Next we need to set up the ACL now for the folder where out logs are going to be stored – we only want admins to view the transcripts not them horrible muggle’s that are users! As there could be sensitive information and the likes from compliant machines.
At this point, I forgot we could of made Logs and Admin Share by using a $, missing a trick like this makes me Grumpy, but I have already done all my screenshots so bah!
Setting ACL in PowerShell while possible and kind straight forward, its pain, and I often just fall back to the GUI to do it. I find it easier! So I won’t bother applying an ACL object to the folder using set-acl… A few clicks of the mouse are faster!
so here are some wonderful screenshots I did of my security folder ACL I won’t bother explaining – it self explanatory. Admins full, Creator Owner denied system full and everyone write and read attributes )… balls I said I wouldn’t explain!
Excellent, then there is the share permission done and dusted – as almost everyone does where I am from, including on training courses and books, we will set the share permission to everyone. Now PowerShell lets you do this with easy unlike with file and folder ACL’s.
Let’s first confirm out permission on the share that we created
as you can see everyone has READ access!
The PowerShell cmdlet that I used to view this was
get-smbshareaccess <sharename> ie logs
Now we can use the PowerShell grant-smbshareaccess cmdlet to provide the everyone user group with full access
grant-smbshareaccess -name logs -accountname everyone -accessright full
It’s nice enough cmdlet to output the results of get-smbshareaccess directly after so we don’t have to confirm…. but Grumpy Admin is Grumpy Admin let’s check anyway!
This time via the GUI!
See wasn’t that simple!
HINT: it being PowerShell, you could pipe the results from get-smbshare object to grant-smbshareaccess 🙂
Done, so we now have our secure storage area for these PowerShell transcripts, now for the easy bit!
Let’s create a group policy that will turn the PowerShell transcription thing on 🙂
The settings we are going to set can be both user or computer, but computer overrides user, so we will just set it there!
So it’s in
[Computer Configuration /Policies/Administrative Templates/Windows Components/Windows PowerShell]
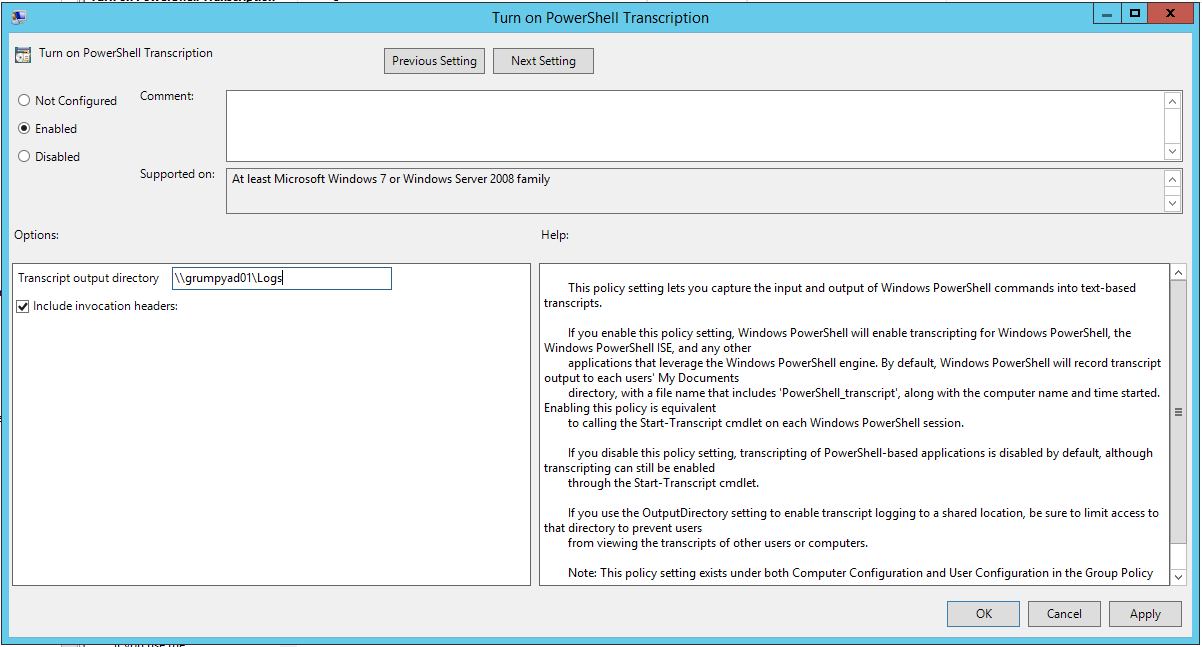
So we going to set both “turn on PowerShell script block logging” and turn on “PowerShell transcription”
In the Transcription – we enable and enter the UNC which we just created in my case it is \\grumpyad01\logs
Save and ensure its enabled and linked to the correct OU – I’m lazy so it’s at the domain level (again it’s a POC and there we go
and here is the proof that it works as per Grumpy Admins Method!
Here is the proof the access controls we put on the log folder prevent a standard user from accessing the logs!
Simple, this means Grumpy Admin can just now wade through the PowerShell transcripts to see how badly his boss codes and what he did to break the network! Troubleshooting time cut in half!
Hazzy