BGINFO - A Posh Recreation
Recently I have been building a lot of Windows Servers in different environments - one
Going through my SANS 508 material I decided to have a closer look at some of the material on the Master File Table ($MFT) in the NTFS file system and how the analysis of it can be used to detect timestamp anomalies (Timestomping)
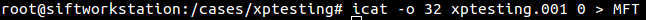
The first thing I wanted to do was extract my MFT so I can then run a tool against it for analysis. As I mentioned in a recent blog we already have the perfect tool called icat which we will use to extract the MFT quickly from our image. We know that in an NTFS file system the MFT always has a record number of 0 (also worthy of note at this point is that the MFT record number is also the inode address for that file) so therefore the following command is what I used to extract the MFT:
SIFT comes pre installed with an old version of the script. To grab the latest and greatest version which allows us to export to Excel without the known issues of the previous version, we download and run from GitHub:
So now I have the script running in my SIFT I want to run it against the MFT which I extracted earlier and to do so I run the following command:
The -e flag is the new addition to the script which allows for the export to an excel format without the corruption to the timings.
The -e flag is the new addition to the script which allows for the export to an excel format without the corruption to the timings.
Once that is completed I open the .csv file on my windows machine with Excel and am presented with a full listing of every MFT entry but more importantly all of the Creation/Accessed and modified times associated with each of its attributes also. Another bonus is we have the record number of each and every file on the system which we can use to carve out any file using icat!
I decided to download timestomp.exe and use it on a file contained within my xp test environment so that I could better show how we can use the output to detect time stomping. Below is a screenshot of the output from analyzeMFT with reference to the file I timestomped:
As you can see the $SI time is before the $FI time which was one of the anomalies I mentioned earlier that we should be looking for.