BGINFO - A Posh Recreation
Recently I have been building a lot of Windows Servers in different environments - one
Setting up an O.MG cable for keystroke injection attacks, and then forensically dumping the firmware for analysis.
The O.MG cable has been commercially available for a while now with a new version and some new firmware being released. I started this analysis when it was first released but have now found the time to finish the research and publish the details looking at the O.MG cable with a Blue Team focus.
This post is going to be in three parts:
The O.MG Cable was conceived and prototyped by @_MG_ . It is designed to look and function like a standard phone charging cable, matching the dimension of official cables like the lighting cables for iPhone and USB-C cables for android devices.
Looks can be deceiving, below the "cheap plastic casing" is a small but powerful chip that is cable of injecting commands in to the Host device it is plugged in to. It also offers Wi-Fi connectivity so it can be remotely controlled. This device is now available for purchase via a partnership with Hak5.
OMG Cable, now also in USB-C and USB Micro.
— _MG_ (@_MG_) February 7, 2020
Get one: https://t.co/Uw4rhWXcNa
Music: @KANGAkult
Logo: @dustrial
Available at: @Hak5 pic.twitter.com/w8QmyYkLMZ
There are plenty of articles that go in to the details of how to program and use an O.MG cable so I am only going to cover the fundamentals here.
First lets plug the cable in to the programmer and plug the programmer in to the laptop.

Then we can clone the official Git repository to get the latest firmware and flash it to our cable.
As you can see in the recording above we set the Wi-Fi details as part of the firmware flash.
For the purposes of this write-up I have set my cable in to Access Point mode so I can use my phone or laptop to connect to the wireless network that is being broadcast by the cable.
This cable can also be configured in client mode where you can give it credentials to an existing Wi-Fi network and it will connect to that network. If using this mode you will either scan the IP range for your cable or, if the network supports it, connect to http://OMG_LASTSIXOFMACID.local
With our customised version of the firmware we can now push some payloads. At this point we need to power the cable without the programmer and wait a few seconds for the access point to become visible.
Once the Access Point is broadcasting we can connect to it using the credentials we set when flashing the device and then from here connect to the Web UI on http://172.16.0.4/ to access all the features of the O.MG cable.
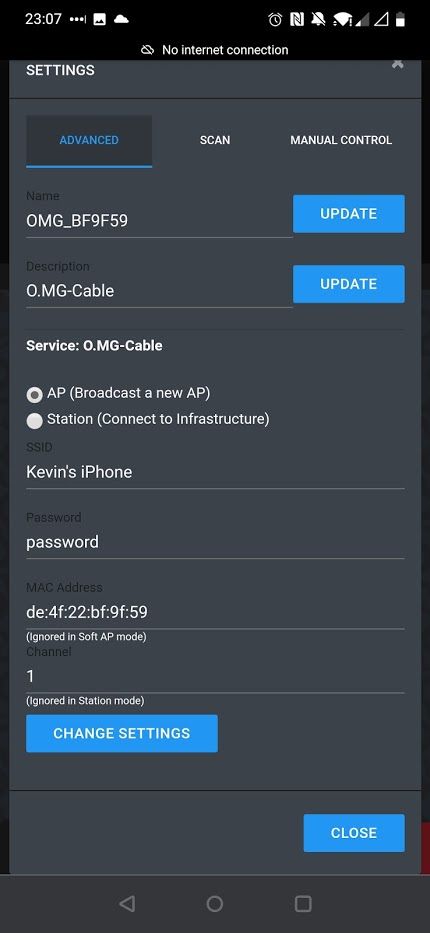
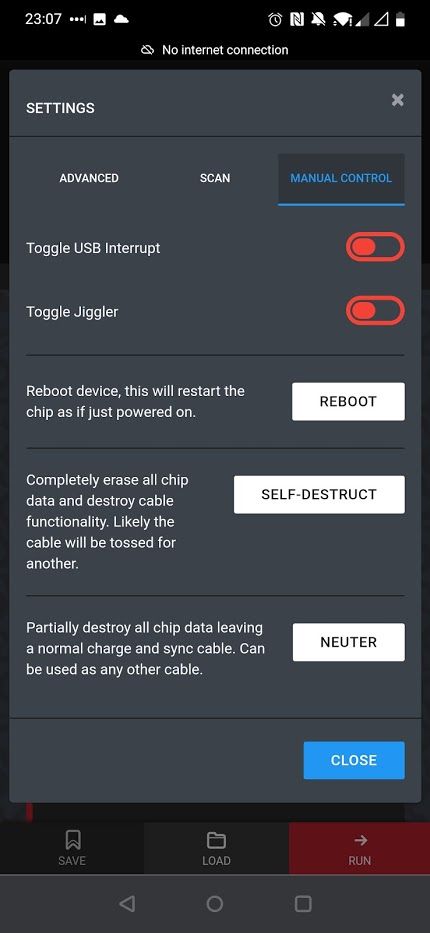
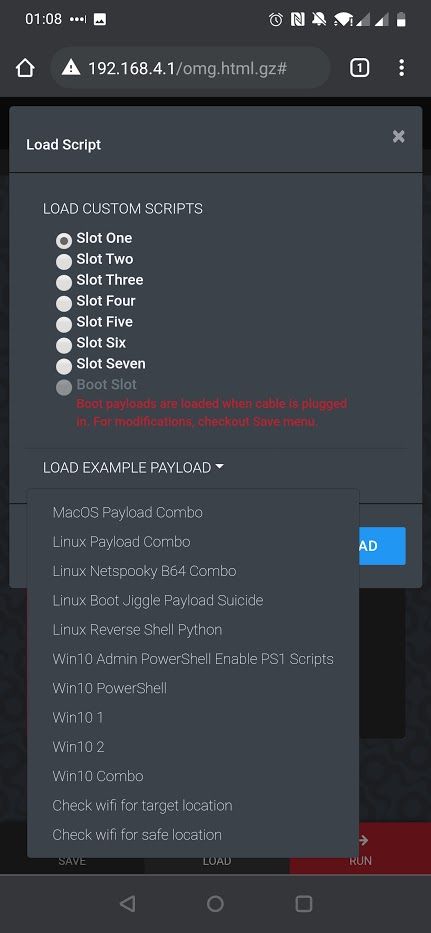
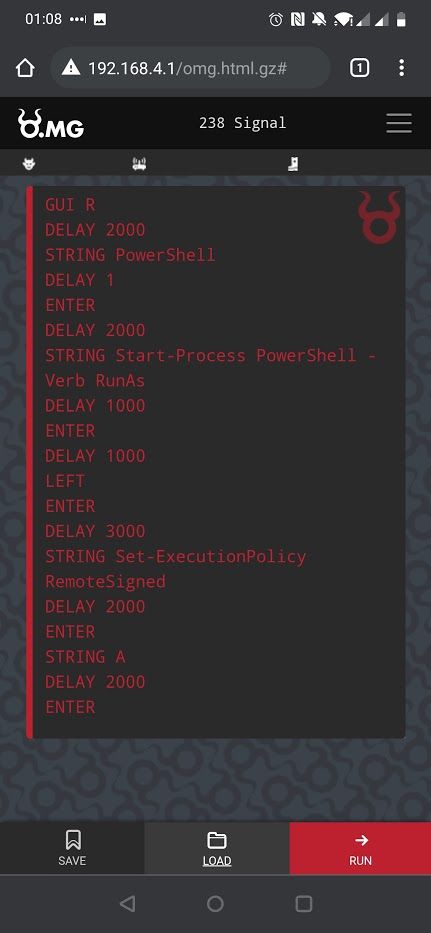
With access to the frontend we can install some payloads and set a default payload to run every time the cable is plugged in to a host.
Once deployed in to the target environment we can connect to the same access point and select which payloads we would like to execute against the victim host.
It is important to note that the cable will only run commands against the computer that the cable is connected to and not the "phone" end of the cable.
In this section we are going to assume the role of a CIRT analyst, we have identified that a users laptop is behaving strangely when a specific cable is plugged in to it. We have recovered the cable and we have access to a programmer.
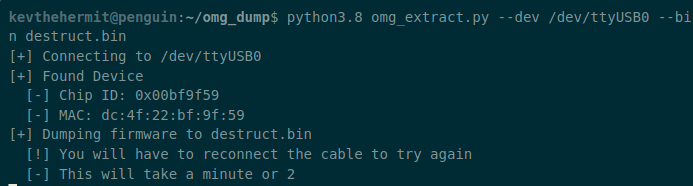
All the details for the cable can be found in the firmware, this includes the Wi-Fi credentials and all the payloads. We can use a custom tool we built to extract the firmware from the cable and then recover useful data from the firmware.
With the Wi-Fi details we can also power the cable locally and access the web interface to recover the payloads and any other custom configuration that may not be picked up by the firmware analysis.
You can find the source code for the omg_extractor on our GitHub https://github.com/Immersive-Labs-Sec/OMG-Extractor we welcome PRs and any suggestions / improvements.
One of the actions the attacker can take is to initiate a self destruct of the cable, if triggered the intended result is that the cable no longer operates as an attack platform and either operates as a normal cable or is rendered completely inert including power.
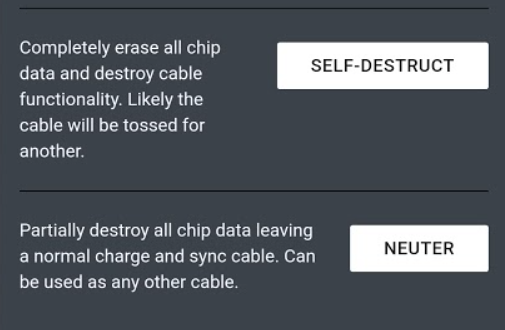
In these instances, despite the message stating "erase all chip data", our firmware recovery tool is still capable of recovering the firmware and all the stored payloads.
There are a couple of techniques we can use to determine if an O.MG Cable is operating in our network. Some techniques can provide full access to the cable, others can only inform us of its presence.
If you have the ability and authority to audit your wireless environment this can be a good place to start. All wireless devices have a MAC address and without getting in to the specifics a portion of this MAC address is used to identify the manufacturer of the wireless chip.
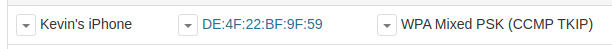
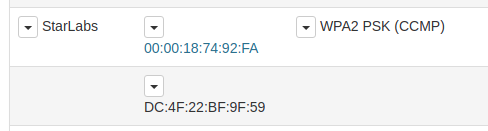
Here we can see our cable in Access Point Mode The vendor portion of the MAC address is slightly different from the one we dumped DE:4F:22 instead of DC:4F:22. Checking the Vendor details we can see that DC:4F:22 is assigned to Espressif Inc a well know vendor for the ESP8266 chip that is used in O.MG Cables.
DE:4F:22 does not appear on a MAC vendor search, however a quick search of WiGLE shows that this vendor ID is commonly associated with ESP chips as well.
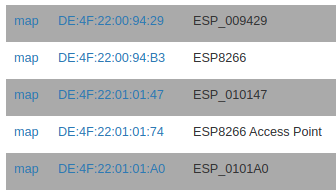
In Station mode we can see the DC:4F:22 Mac address has connected to our Wi-Fi network as a client.
If the cable is connected in Station Mode we can now check DHCP logs, identify the IP address allocated to this cable and we can access the Web UI remotely in the same way an attacker could. To identify what device the cable is plugged in to you could consider sending your own payload to the host. This Ducky script example will open notepad and enter a message.
DELAY 2000
GUI r
DELAY 1000
STRING notepad.exe
ENTER
DELAY 750
STRING Please contact the Security team on security@companyname.comIf you are not able to perform a wireless audit you may be able to scan the local network looking for cables in Station mode.
This nmap script is capable of scanning local networks and extracting data via the Web Socket that is used by the O.MG interface.
If you are feeling very adventurous you can grab a copy of the web-socket CLI tool and gather more information from the cable.
Update
Since this article was published an updated firmware has been released that fixes the "Self Destruct" feature. You can read more on that here - https://mg.lol/blog/autonomy-anti-forensics-with-the-o-mg-cable/