
Grep and icat
Just a very brief blog post regarding the power of grep and icat in relation to forensic images. I am currently revising for my GCFA certification and as part of this revision was

Just a very brief blog post regarding the power of grep and icat in relation to forensic images. I am currently revising for my GCFA certification and as part of this revision was

In Part 1 of this blog I mentioned the metadata regarding one of the separate files contained within the deleted cache. I stated that I would further explain what is contained within that
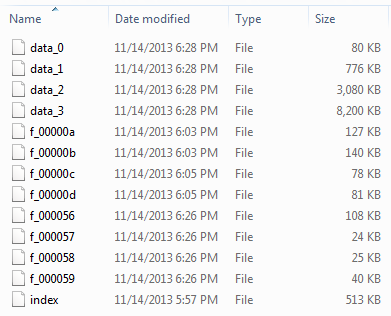
As part of my ongoing training I have been fortunate enough to start down the road towards an MSc in Forensic Computing for Practitioners with De Montfort University, Leicestershire. We have been taught
As I lie here having finished another SANS Course this time the 508 Advanced Computer Forensic Analysis and Incident Response, it occurs to me that everyday is and always will be a learning
Most malware is designed to reach back out to the internet, either to wait for further instructions or to send data back to the bad guys. Sometimes we want to allow this to