Analysing an O.MG cable
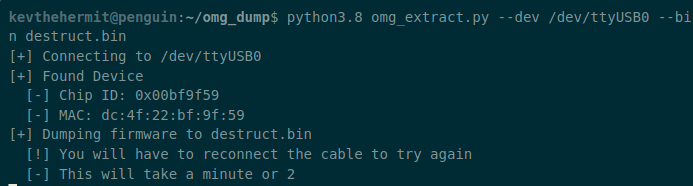
Setting up an O.MG cable for keystroke injection attacks, and then forensically dumping the firmware for analysis.
The O.MG cable has been commercially available for a while now with a new version and some new firmware being released. I started this analysis when it was first released but have now found the time to finish the research and